I’ve seen a lot of questions around configuring CA signed certificates with vCloud director and how to avoid those “Cryptographic Errors” when starting the vCloud director service. In this post I hope to go through the configuration and setup vCloud director to use CA signed certificates.
Before we get into the details some information about the environment. I have an Intermediate certificate server and a Root certificate server, we will be issuing certificates from the intermediate certificate server but will require the complete chain to be imported in the vCloud director keystore.
Using keytool we will create the keystore and generate the CSR’s. Its recommended to use the keytool shipped with vCloud Director which is located at /opt/vmware/vcloud-director/jre/bin/keytool.
1. Create the keystore and generate a certificate for the http service
2. Create the certificate signing request file for the http service
3. Generate a certificate for the console proxy service
4. Create the certificate signing request for the console proxy service
There should now be 2 CSR files created for the http and console proxy service that needs to be submitted to the CA. You can copy the contents of the CSR file by running ‘cat’ on the file.
5. On the Intermediate certificate server or the Root Certificate server navigate to the Web enrollment page, http://hostname/certsrv . Select Request a New certificate, choose the Advanced certificate request and select Submit a certificate request by using a base-64 encoded CMC or PKCS.
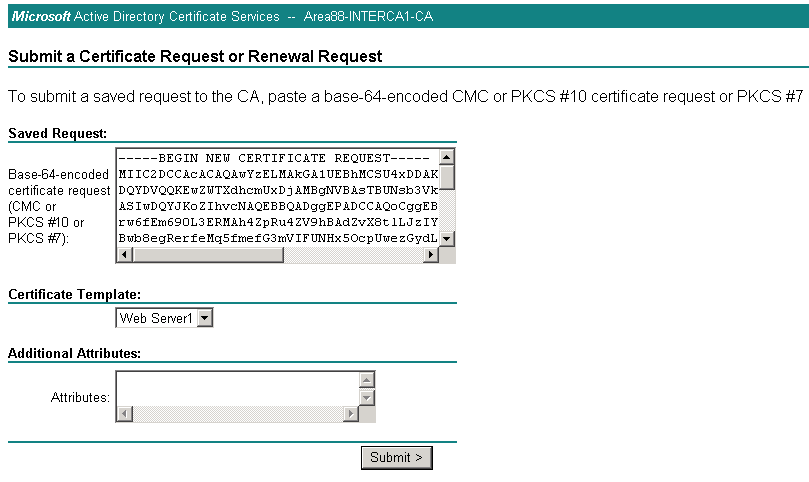
6. Paste the contents of the http CSR file in the Saved Request field. Select WebServer for the certificate template and click submit.
7. Select DER encoded and Download the certificate
8. Repeat steps 6 & 7 for the console proxy CSR
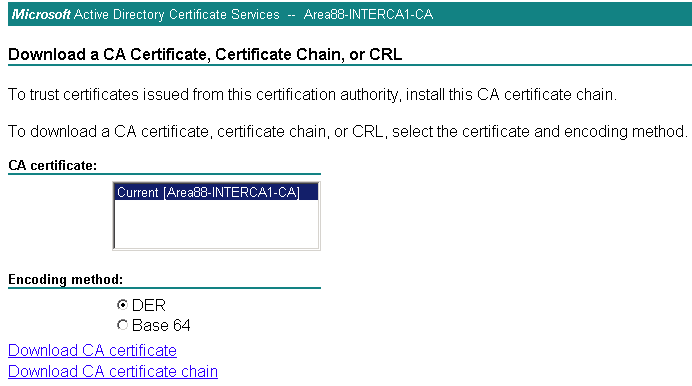
9. With the certificates for http and console proxy generated we also need the root certificate and the intermediate certificate. From the Web Enrollment page download the root certificate and the intermediate certificate
10. Now that we have the certificate chain we need to import the complete chain into the keystore.
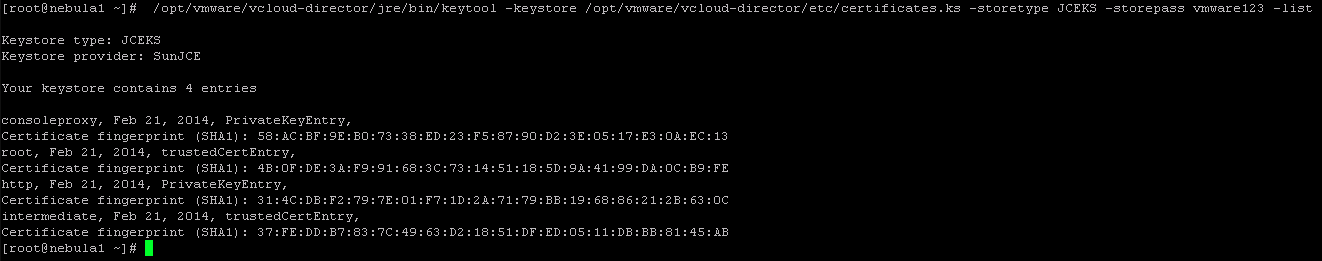
11. We can verify that we have all the certificates imported into the keystore using the below command. You can also validate the thumbprint for each certificate from the keystore with the downloaded certificate
12. Run the vcloud director configure script and provide the path to the keystore file
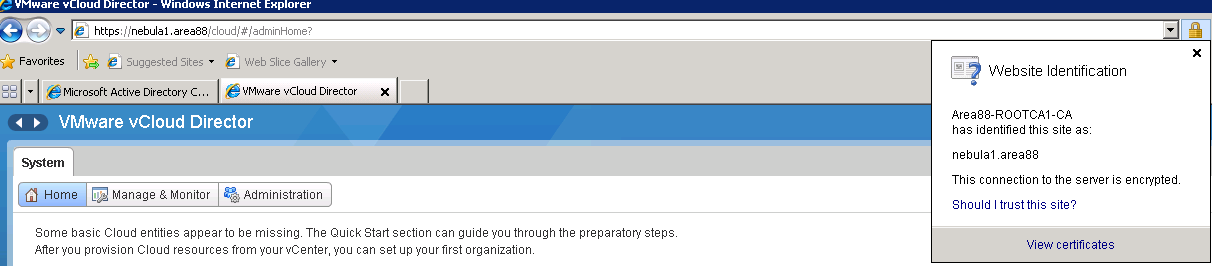
13. Access the vCloud Director web page and notice that the certificate should be trusted.
Michael Webster has already made a blog post on configuring CA signed certificates for vShield Manager which you can find here
I hope this blog post is useful and helps overcome the certificate pain that we run into. Thank you for reading.