In this short post we will look at capturing packets that are encapsulated with the VXLAN protocol and how to decode them with wireshark for troubleshooting and debugging purposes. This procedure is handy when you want to analyze network traffic on a logical switch or between logical switches.
In order to capture packets on ESXi we will use the pktcap-uw utility. Pktcap-uw is quite a versatile tool, allowing to capture at multiple points on the network stack and even trace packets through the stack. Further details on pktcap-uw can be found in VMware product documentation –here
The limitation with the current version of pktcap-uw is that we need to run 2 sets of commands to capture both egress and ingress. With that said lets get to it.. In this environment I will capture packets on vmnic4 on source and destination ESXi hosts.
To capture VXLAN encapsulated packets egressing uplink vmnic4 on the source host
To capture VXLAN encapsulated packets ingressing uplink vmnic4 on the destination host
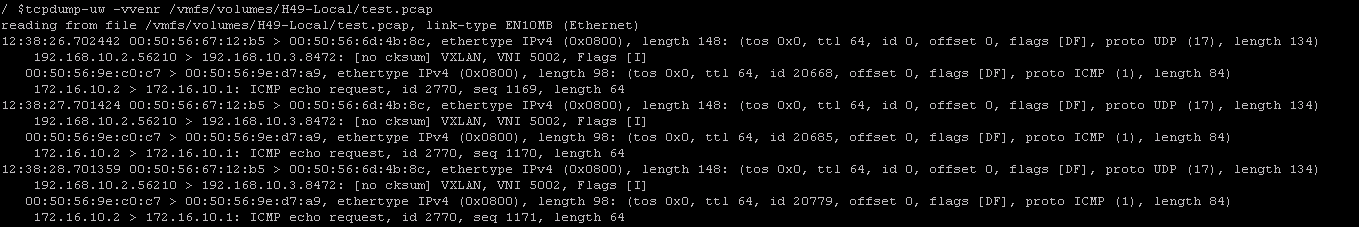
If you have access to the ESXi host and want to look at the packet capture with the VXLAN headers you can use the tcpdump command like so,
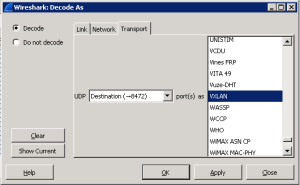
This capture can further be imported into wireshark and the frames decoded. When the capture is first opened wireshark displays only the outer source and destination IP which are VXLAN endpoints. We need to map destination UDP port 8472 to the VXLAN protocol to see the inner frames
To do so, open the capture with Wireshark –> Analyze –> Decode As
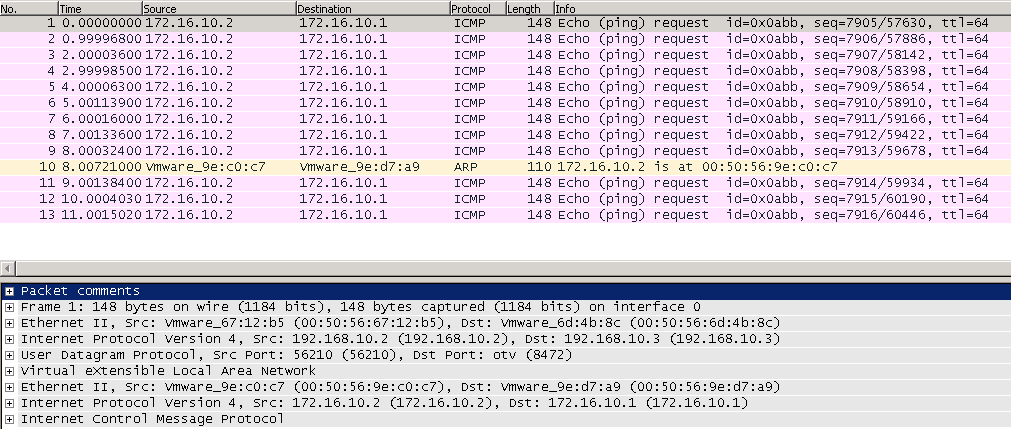
Once decoded wireshark will display the inner source and destination IP address and inner protocol.
I hope you find this post helpful, until next time!!